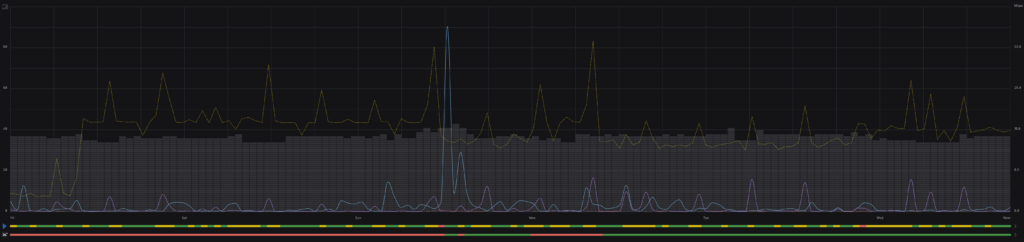
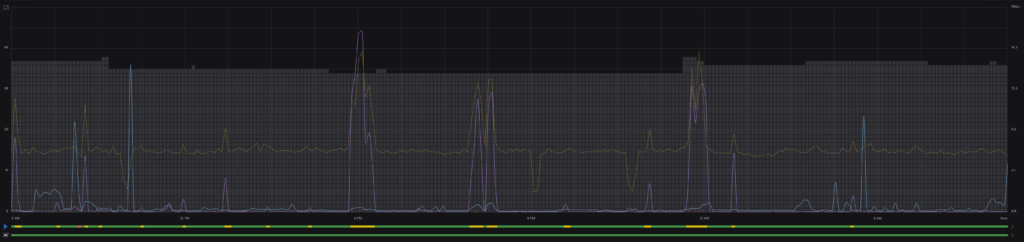
This is was a long time coming. i’ve had the equipment for years, but it was always needed elsewhere. Finally home, it’s up and running. smoother and more reliably than with any previous deployment. Just in time for me to accidentally unplug my Spectrum modem!
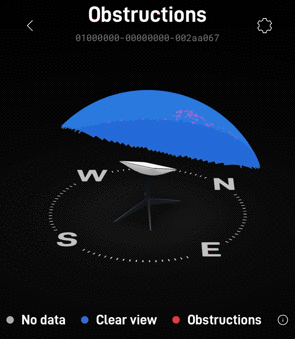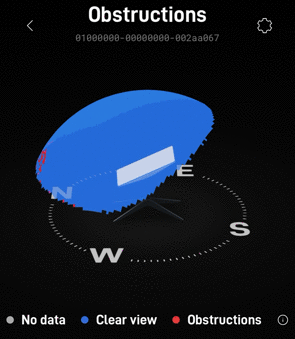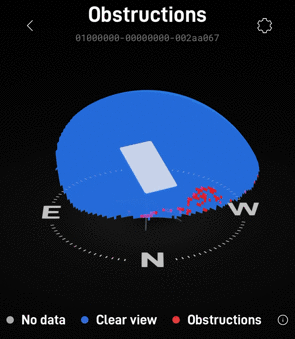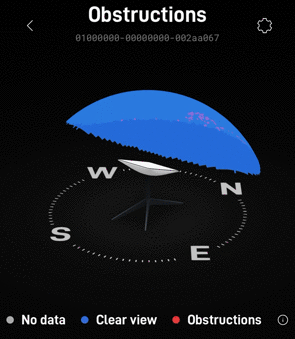
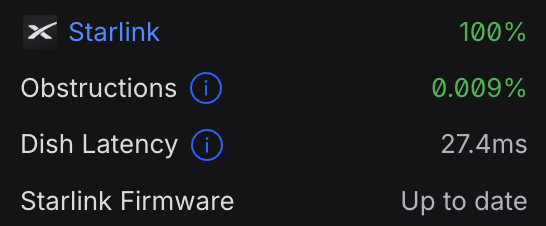
I was surprised and impressed by the integration with the Starlink that Unifi exhibited. including obstruction info and firmware info on the Unifi dashboard.