@kismetwireless@infosec.exchange dropped a new kismet on us in time for #WWWD (World Wide War Drive). With much anticipated Night Mode UI. i have to admit, i was so desperate for this, my display had to be covered at night. now it looks amazing! thanks Dragorn!
Tag: raspberry Pi
The antennas are back! Wardriving in a Tesla.

This project was cannibalized over a year ago. With Raspberry Pi as difficult to get ahold of as they’ve been, i thought this project might never come back to life. I launched a number of pi liberating ideas with some success. I now have enough for both fun personal projects and to get my work done. I felt i should explain the name wardriving. It is a variation on wardialing. Wardialing was trying phone numbers, looking for interesting things on the phone. Wardriving is similarly driving around looking for interesting things in the air.
My wardriver is not pictured above, but these Pi are ready for whatever comes next. I’ve recovered an assortment of different Pi from original B+ (pi-hole) to a 2GB Pi 4 (broken helium miner). One of the best parts of this setup is the early Pi 3 (not B+). This was a lucky find as it consumes less energy and produces much less heat. With only 6 radios running (including GPS) the lower performance hasn’t been an issue, but the reduced power has been incredible. Early testing has me getting an additional 20-40% battery life vs the original pi 4 configuration. my cable management has also improved with this iteration. The setup fits in a small box in my trunk instead of a tangled mass of wires in a large bin (prototyping is fun). The reason power is so important because, believe it or not, the amperage you can pull out of a Tesla for accessories is limited. Without an alternator dumping piles of unclean energy i am forced to resort to BYOB (bring your own battery). I got a monster battery to power the Pi 4 and even more radios and accessories of the original prototype.
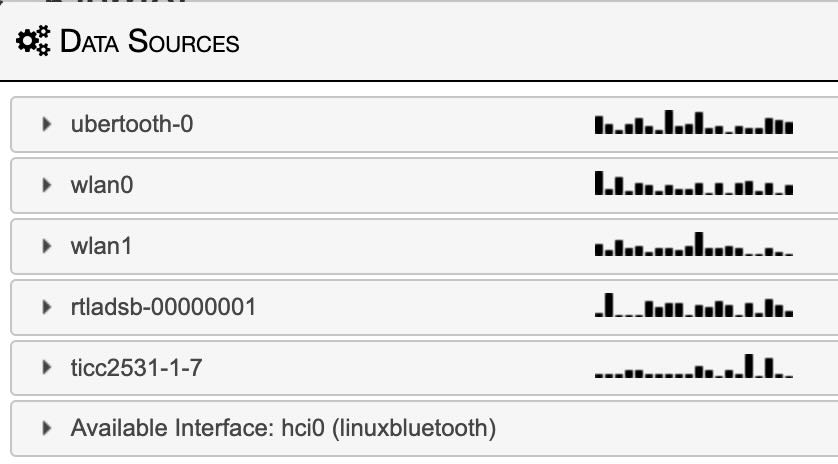
It is fun using the ADSB live tracker in Los Angeles as there are always planes above. Next step will be DJI drone tracking and some sort of dashboard indicator/control. I started a WiGLE account, it’s off to a pretty good start. i found a few APs, but i’m still figuring out how to share BT. maybe i’ll join the #HardHatBrigade group.




my Asterisk PBX is back!
 After Google killed XMPP support for Google Voice, I no longer had a house phone. I was using my Google Voice number as a home phone and for the gate info our building. This lead to the whole system being ignored and neglected. By the time the SD card gave up the ghost, even the backups were in poor shape. I rebuilt the whole system fresh from the latest RasPBX dist and it’s working better then ever. Bought a real DID so i could continue to use Google Voice on our handsets at home. It’s great to have my Asterisk back.
After Google killed XMPP support for Google Voice, I no longer had a house phone. I was using my Google Voice number as a home phone and for the gate info our building. This lead to the whole system being ignored and neglected. By the time the SD card gave up the ghost, even the backups were in poor shape. I rebuilt the whole system fresh from the latest RasPBX dist and it’s working better then ever. Bought a real DID so i could continue to use Google Voice on our handsets at home. It’s great to have my Asterisk back.
Introducing DEFCam or how i made a hat for DEFCON!
This is a silly project that i have spent probably too much time on. First I thought, why not time-lapse my upcoming defcon trip. Then i thought, why not live stream it. So… I started with a Pi Zero and a Pi Camera v1. Wired some pins to the GPIO for power. Made a custom wire and hot glued it into the hat. Done!
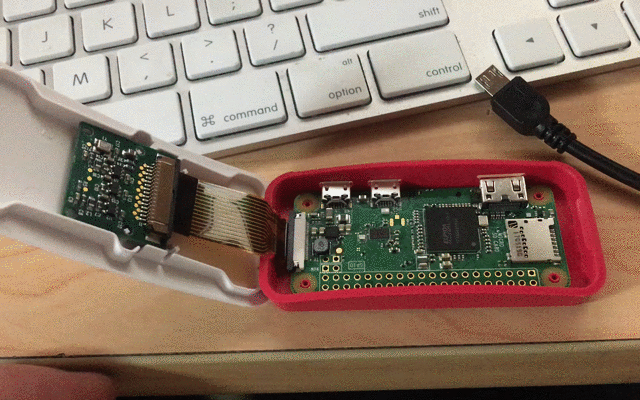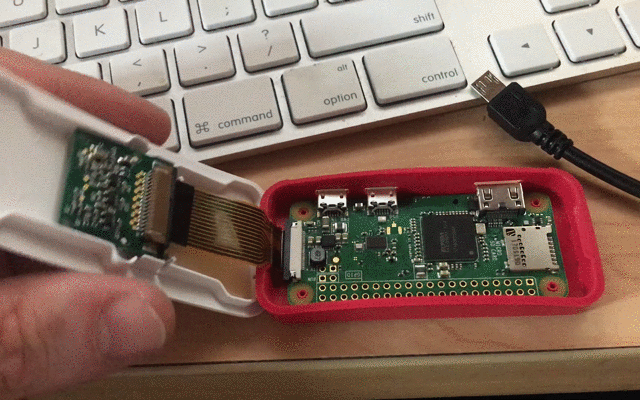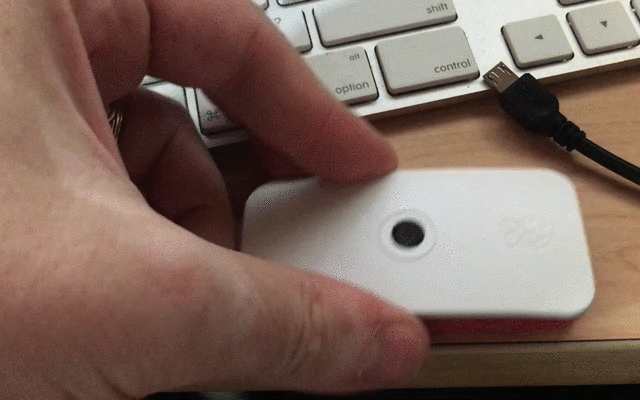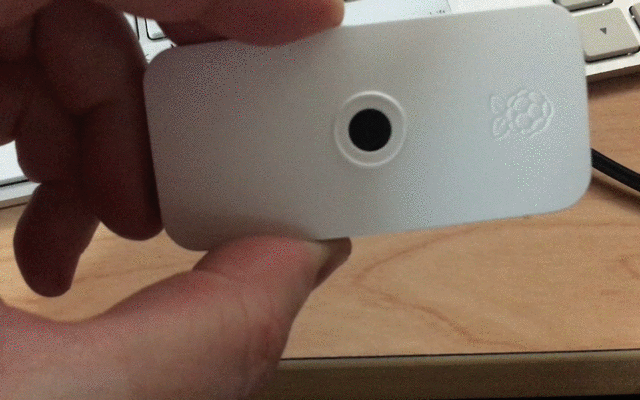



Monitoring power usage is sometimes my only insight.
I have been working on a number of Raspberry Pi projects in various stages of working. To distract from more difficult projects (not to mention nostalgia and fun) I have been building an Adafruit PiGrrl portable classic game emulator. At several points with this project or other without a lot of feedback from the device I’m working with, I’ve relied on milliamp readings from the Mico USB Cable/Voltage Display. This tiny bit of information is incredibly helpful in determining what my Pi is up too. Idle? Booting? Overwhelmed? In the land of the blind the one eye’d man is king. At the very least it reduced the total time waisted waiting on crashed or other broken attempts.

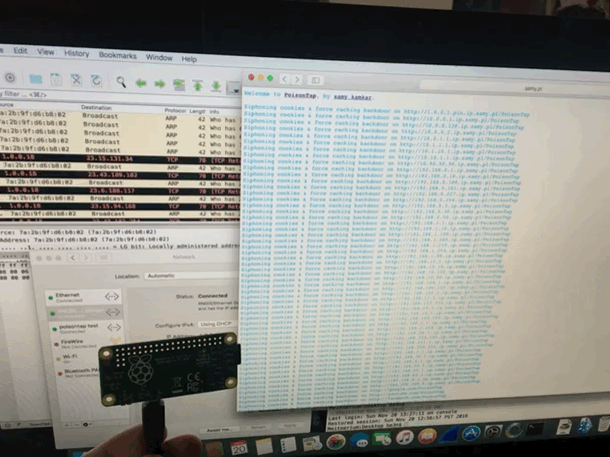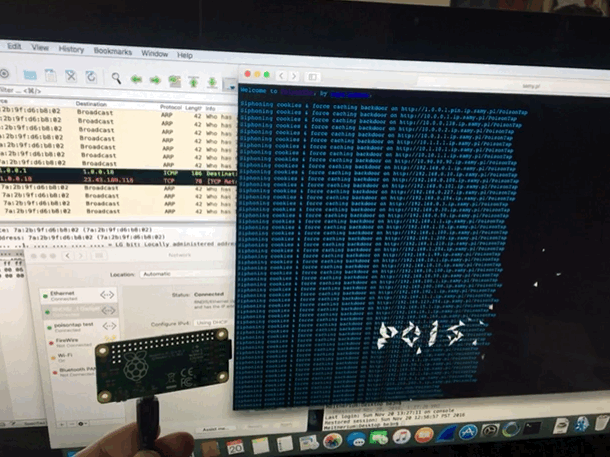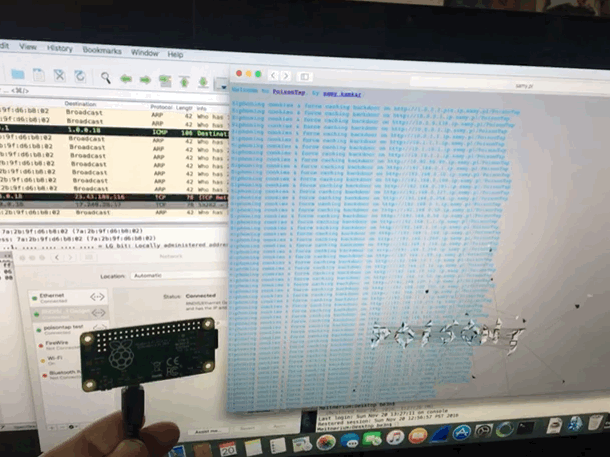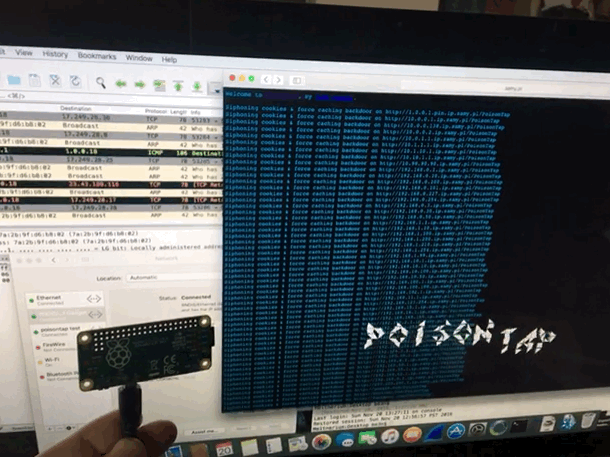
Played with PoisonTap network hijacking tool
@SamyKamkar made an impressive and terrifying tool. This simple USB device steals your cookies, poisons your cache, and even persists a web backdoor. On a locked machine no less! It depends much on the trust that our computers take for granted. Trusting a USB device is not up to no good. Trusting the local network not trying to confuse. We must reexamine this trust going forward. It didn’t take long to get it up and running, however once you do, you can spend hours tinkering. (i was working to combine it with @mubix‘s work here)
I am also delighted to have my first Raspberry Pi as a USB device rather then host. it is certainly exciting to create some new doodads using this dangerous toolkit.
UPDATE
I have since made a version without the cache attack. I completely failed to steal the poisontap visuals, but TheCodePlayer offers offered a delightful matrix animation. next step is to man in the middle ssl too. I’m turning it into a device that logs everything while connected, but doesn’t persist.