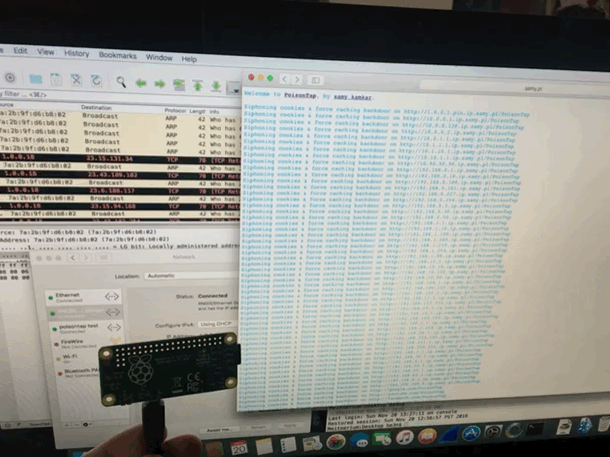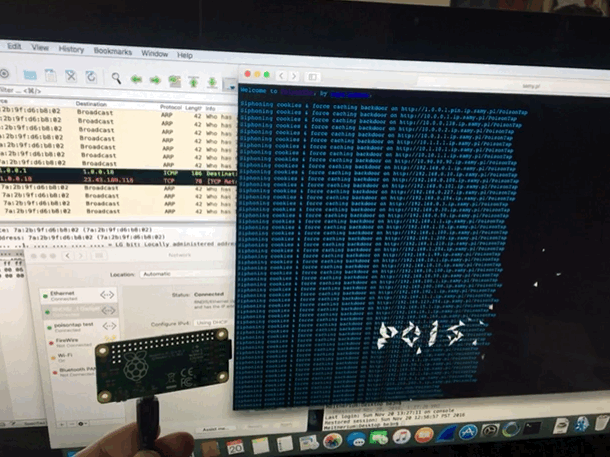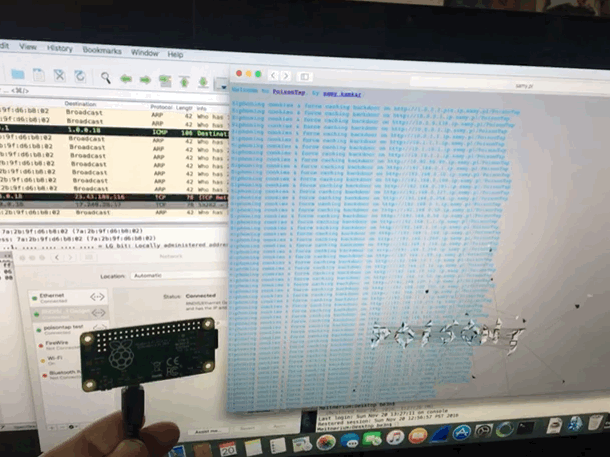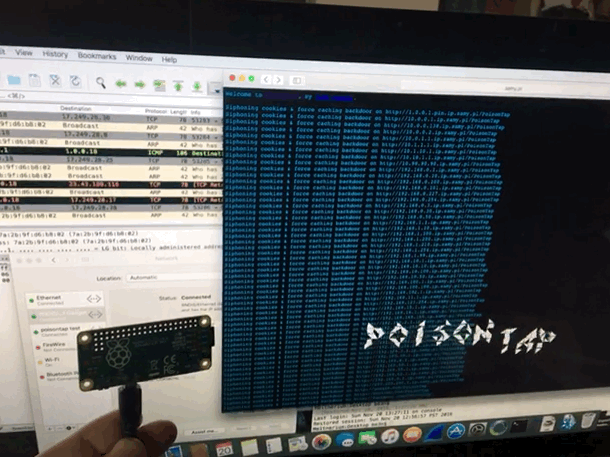
@SamyKamkar made an impressive and terrifying tool. This simple USB device steals your cookies, poisons your cache, and even persists a web backdoor. On a locked machine no less! It depends much on the trust that our computers take for granted. Trusting a USB device is not up to no good. Trusting the local network not trying to confuse. We must reexamine this trust going forward. It didn’t take long to get it up and running, however once you do, you can spend hours tinkering. (i was working to combine it with @mubix’s work here)
I am also delighted to have my first Raspberry Pi as a USB device rather then host. it is certainly exciting to create some new doodads using this dangerous toolkit.
UPDATE
I have since made a version without the cache attack. I completely failed to steal the poisontap visuals, but TheCodePlayer offers offered a delightful matrix animation. next step is to man in the middle ssl too. I’m turning it into a device that logs everything while connected, but doesn’t persist.
 For years now I have been terrified of one particular network device. This high end device requires a service contract from it’s manufacturer to be eligible for software upgrades and as such had been neglected for some time. I couldn’t use it the way I wanted or hardly at all for fear that it would be compromised via the Heartbleed vulnerability. Forced to relegate this amazing appliance to be firewalled far from the prying packets of the Internet at large.
For years now I have been terrified of one particular network device. This high end device requires a service contract from it’s manufacturer to be eligible for software upgrades and as such had been neglected for some time. I couldn’t use it the way I wanted or hardly at all for fear that it would be compromised via the Heartbleed vulnerability. Forced to relegate this amazing appliance to be firewalled far from the prying packets of the Internet at large.