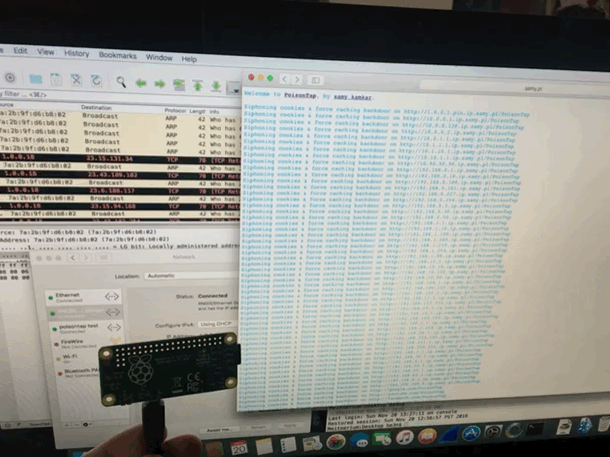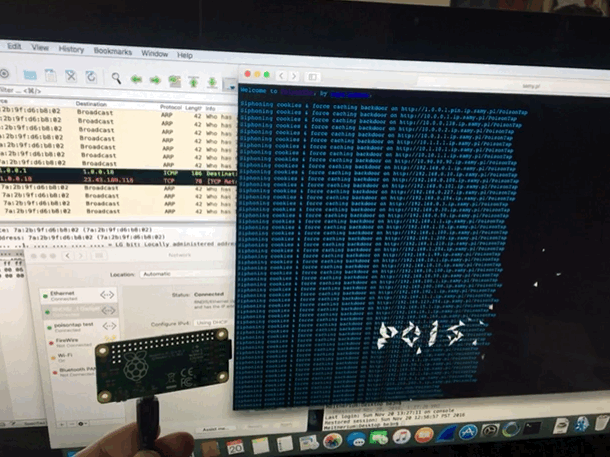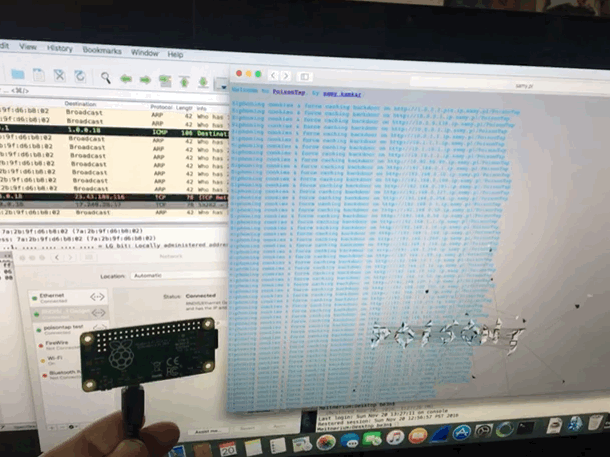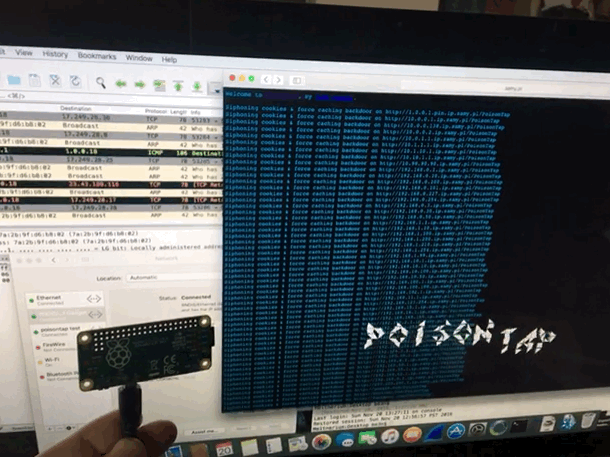
UPDATE: this is all outdated, go here.
I have been consolidating some of my sites onto a single hosted Unifi controller. Documentation was outdated so I am going to post some useful info here. My original plan was to setup a basic apache2 site, use certbot to generate my certificates and then install them into the Unifi controller. The first frustration is that you cannot simply install the certs you want into the unifi controller. second frustration, java. once you get over that, it’s super easy.
I had some issues with the initial migration. i ended up having to start over. handy command to remove unifi controller with all it’s configuration and data. apt-get remove unifi --purge Just remember, you will need to reinstall Unifi after. It will be bran new and back to the wizard.
Getting started with SSL, I learned mostly from here. First create a CSR with unifi through command line…
cd /usr/lib/unifi
java -jar lib/ace.jar new_cert <hostname> <company> <city> <state> <country>
this creates unifi_certificate.csr.der and unifi_certificate.csr.pem inside the data directory where you already are (/usr/lib/unifi/). Now we need to feed the CSR into certbot. Note that at this point, i already have apache2 installed with a very simple virutalhost and site setup with the domain i am creating a cert for. Here is the command to feed the CSR generated by Unifi into certbot to be certified:
certbot certonly --apache --csr /usr/lib/unifi/data/unifi_certificate.csr.der
Certbot will make sure that domain is yours (and your apache config is working) and then output a signed cert and a chain that is almost everything you need to install the certificate back into the Unifi controller. Still in /usr/lib/unifi/data/ 0000_cert.pem is my signed cert and 0001_chain.pem is my signed cert plus the intermediate certificate. what’s missing is Let’s Encrypt’s Root certificate to validate the intermediate certificate and thus complete the chain of trust.
Continue reading “Hosted Unifi controller with Let’s Encrypt SSL!” →
 Continue reading “My first purchase from a KeyMe kiosk and I have notes!”
Continue reading “My first purchase from a KeyMe kiosk and I have notes!” 

 Believe it or not, my home network actually used Radius authentication many years ago. Before I got a Nest (which still cannot connect to anything that isn’t open, WEP, or WPA/WPA2). At the time, I assumed the Nest app talked directly to the thermostat. Not true. It just needs internet to talk to it’s servers where it receives the commands and preferences from the app. Armed with that knowledge and
Believe it or not, my home network actually used Radius authentication many years ago. Before I got a Nest (which still cannot connect to anything that isn’t open, WEP, or WPA/WPA2). At the time, I assumed the Nest app talked directly to the thermostat. Not true. It just needs internet to talk to it’s servers where it receives the commands and preferences from the app. Armed with that knowledge and  I just assumed that the problem was related to my recent SSL renewal. Turns out, Google security recently published
I just assumed that the problem was related to my recent SSL renewal. Turns out, Google security recently published