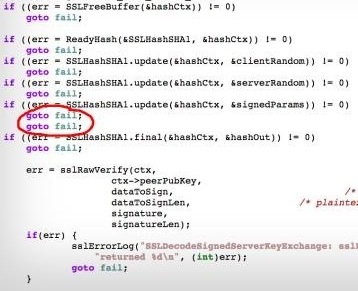
 The security community went into a frenzy this weekend over Apple’s latest iOS security update. On Friday, Apple quietly released iOS 7.0.6 and 6.1.6 to patch a bug in its SSL implementation. This particular bug nicknamed “goto fail” for the actual contents of its source code behind the error. Basically, one too many goto fail causes the fail not to be conditional, but absolute. This failure allows Apple’s SSL framework (the technology that secures web transmissions) to be easily bypassed. In other words, Safari, Mail, Calendar, Software Update, as well as any 3rd party applications who take advantage of Apple’s SSL libraries could potentially have their communications intercepted by an unscrupulous individual. Apple claims that it is a type-o, but many wonder if this might be a deliberate backdoor (one that has lasted over a year).
The security community went into a frenzy this weekend over Apple’s latest iOS security update. On Friday, Apple quietly released iOS 7.0.6 and 6.1.6 to patch a bug in its SSL implementation. This particular bug nicknamed “goto fail” for the actual contents of its source code behind the error. Basically, one too many goto fail causes the fail not to be conditional, but absolute. This failure allows Apple’s SSL framework (the technology that secures web transmissions) to be easily bypassed. In other words, Safari, Mail, Calendar, Software Update, as well as any 3rd party applications who take advantage of Apple’s SSL libraries could potentially have their communications intercepted by an unscrupulous individual. Apple claims that it is a type-o, but many wonder if this might be a deliberate backdoor (one that has lasted over a year).
The real tragedy of this issue is that it effects Mavericks (Mac OS 10.9.x) as well as iOS, but there is yet no official fix for Apple Computers. Update Published by Apple! Apple desktops, laptops, and iMacs are now were left in a very dangerous position: unprotected to a known threat. I am sure that the bad guys are already configuring their sslstrip, sslsniff, or similar tools. Accounts will be compromised, communications will be intercepted or manipulated, or in the case of software updates, malware could even be introduced.
What can we do? First off, run the 7.0.6 update on any iOS devices not yet up to date. Do this from a trusted wifi, not a public one. With your mac, avoid public wifi until this is resolved. Avoid Apple Mail except when absolutely necessary and only from trusted networks. Only use Google Chrome for secure web browsing (it uses its own SSL framework). Optional: Install @i0n1c’s binary patch. @i0n1c’s patch fixes the bug, but may break other things. Run Apple 10.9.2 update!
links:
Test your system: https://gotofail.com/
Great Writeup: https://www.imperialviolet.org/2014/02/22/applebug.html
Quick & Dirty Patch: http://www.sektioneins.de/en/blog/14-02-22-Apple-SSL-BUG.html
Official Apple Fix http://support.apple.com/kb/HT6150











 The security community went into a frenzy this weekend over Apple’s latest iOS security update. On Friday, Apple quietly released iOS 7.0.6 and 6.1.6 to patch a bug in its SSL implementation. This particular bug nicknamed “goto fail” for the actual contents of its source code behind the error. Basically, one too many goto fail causes the fail not to be conditional, but absolute. This failure allows Apple’s SSL framework (the technology that secures web transmissions) to be easily bypassed. In other words, Safari, Mail, Calendar, Software Update, as well as any 3rd party applications who take advantage of Apple’s SSL libraries could potentially have their communications intercepted by an unscrupulous individual. Apple claims that it is a type-o, but many wonder if this might be a deliberate backdoor (one that has lasted over a year).
The security community went into a frenzy this weekend over Apple’s latest iOS security update. On Friday, Apple quietly released iOS 7.0.6 and 6.1.6 to patch a bug in its SSL implementation. This particular bug nicknamed “goto fail” for the actual contents of its source code behind the error. Basically, one too many goto fail causes the fail not to be conditional, but absolute. This failure allows Apple’s SSL framework (the technology that secures web transmissions) to be easily bypassed. In other words, Safari, Mail, Calendar, Software Update, as well as any 3rd party applications who take advantage of Apple’s SSL libraries could potentially have their communications intercepted by an unscrupulous individual. Apple claims that it is a type-o, but many wonder if this might be a deliberate backdoor (one that has lasted over a year).
