This post should prove it. Thanks to @joedolson for graciously not being offended when i suggested it was a problem with his code. My own idiocy omitted an essential file. whoops! must test more throughly before I bother others.
Category: Web
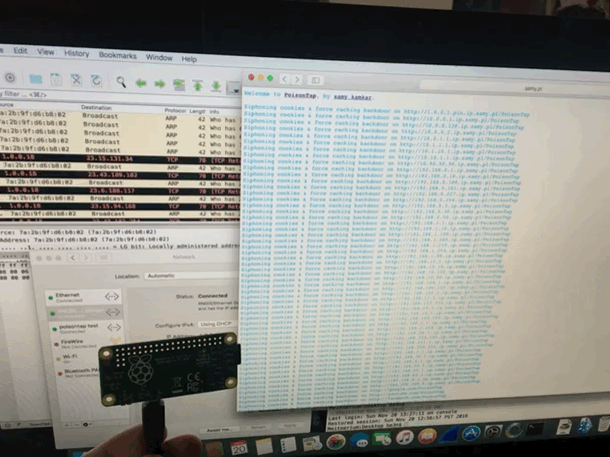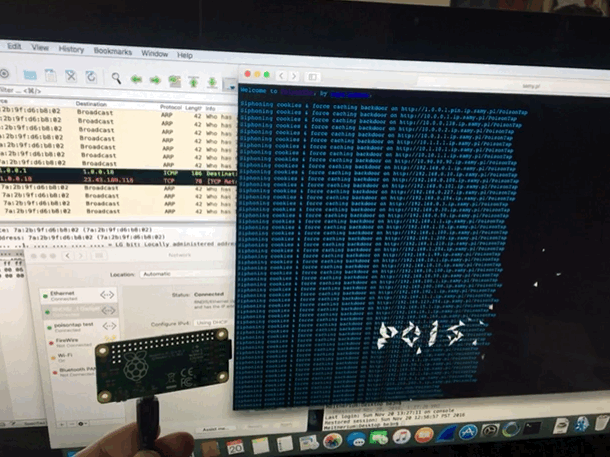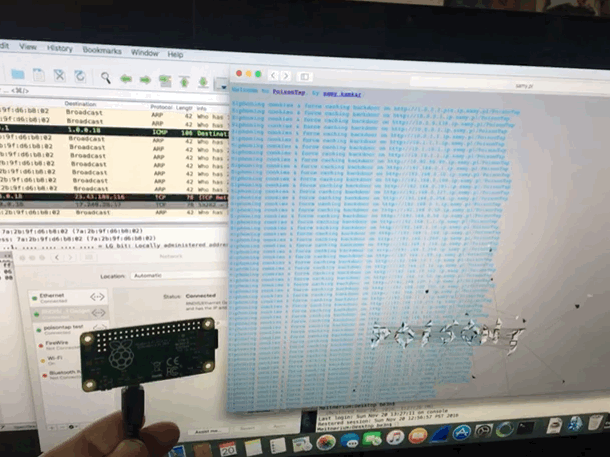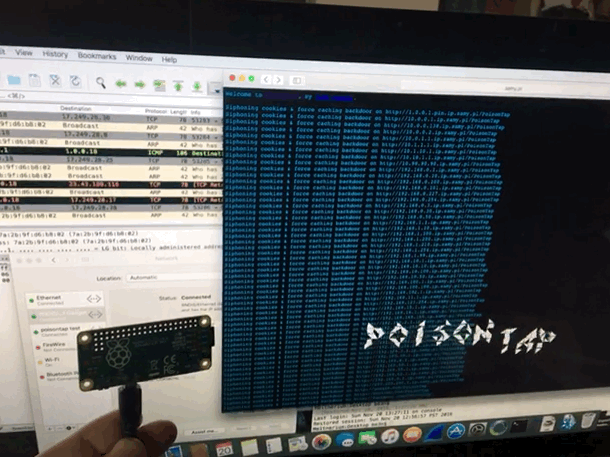
Played with PoisonTap network hijacking tool
@SamyKamkar made an impressive and terrifying tool. This simple USB device steals your cookies, poisons your cache, and even persists a web backdoor. On a locked machine no less! It depends much on the trust that our computers take for granted. Trusting a USB device is not up to no good. Trusting the local network not trying to confuse. We must reexamine this trust going forward. It didn’t take long to get it up and running, however once you do, you can spend hours tinkering. (i was working to combine it with @mubix‘s work here)
I am also delighted to have my first Raspberry Pi as a USB device rather then host. it is certainly exciting to create some new doodads using this dangerous toolkit.
UPDATE
I have since made a version without the cache attack. I completely failed to steal the poisontap visuals, but TheCodePlayer offers offered a delightful matrix animation. next step is to man in the middle ssl too. I’m turning it into a device that logs everything while connected, but doesn’t persist.
There may be too many animated Gifs on my website.
This post will bump the largest one off the front page. My site was getting a bit bloated.
Sorry Facebook Users.
 I broke all the links from my previous posts to Facebook. sorry. honestly, I should have updated my syndication years ago. I am not going to delete the posts, but they will just link to the current site. Lets faec it, no one was clicking on it anyway. whoops.
I broke all the links from my previous posts to Facebook. sorry. honestly, I should have updated my syndication years ago. I am not going to delete the posts, but they will just link to the current site. Lets faec it, no one was clicking on it anyway. whoops.
Something is getting better!
![]() My blog is now distributed with Amazon’s Cloudfront CDN using powerful encryption and signed by a proper CA certificate. See the shiny green lock? Like a grown-up adult website. After only 8.5 years. Congratulations! Thank you StartSSL!
My blog is now distributed with Amazon’s Cloudfront CDN using powerful encryption and signed by a proper CA certificate. See the shiny green lock? Like a grown-up adult website. After only 8.5 years. Congratulations! Thank you StartSSL!
Update: you may have noticed that the transition has been a bit bumpy. Still getting the hang of things and this website needs a lot of work (possibly a complete resurfacing). I am sorry about the downtime and all the SSL errors, I am working on it. Thanks Eric, I hope I didn’t step on your birthday plans kidnapping your brain.
Dreamhost you made a fool of me.

I recommended Dreamhost highly for many years. When Mac Enthusiasts asked me where they should host their email, I said Dreamhost without a pause. We moved the MX record over the weekend from Media Temple to Dreamhost and waited as the DNS records propagated throughout the internet. Monday morning I left everyone’s new credentials on a note so they could get to work. Immediately, we noticed a problem. The mail server was unresponsive. By noon, I had a good understanding of the problem and I submitted a support request. Dreamhost did not respond until after 9pm and this was all they said.
I’m terribly sorry for the issues with the mail service responding slowly today. It looks like there was an issue with our POP/IMAP machines causing the slowness with the accessing of your mailbox earlier today. Our Admins were able to look into this matter and get the issue resolved. This was a temporary issue with the mail load spiking, resulting in the slowness, but that’s all resolved now.
Oh good one might think. Problem reported, problem solved. Not so. Of course now that buisness was done, I couldn’t verify their claim. Again I waited to see if their claim was true. It was not. It the light of Tuesday morning macenthusiasts.com email was completely unusable from the office. So once again, I carefully composed my support request. They quickly responded with additional questions, I immediately answered. They wanted the IP of the office and a traceroute to their mail server. No response from Dreamhost until 1am. This is what they said:
This should be resolved with the load balancing issues resolved. I just checked multiple email addresses from your domain, and was able to connect to them on multiple ports. I also checked and found that your office IP address is not currently banned. I am sorry it took so long to get back to you, your tickets were placed in my queue when I was out of
the office. Please let us know if the issues are continuing in the office, so we can continue to look at the office, and troubleshoot there.
My first domain is mine again! muhahaha!
 Back in 1997, I registered my first domain benforpresident.org. It was a silly site that I would do almost nothing with. I had grand plans for a genuine run for 2016. With technology on my side, how could I fail? Well, I missed a registration payment and it was snatched from me. Oddly, the content remained the same in the hands of it’s new owner. Nothing was added, nothing was changed. (apart from some tracking javascript). Yesterday on a whim, I checked it’s availability and reacquired it. I don’t know exactly what I am going to do with it, but for now, I have set the clock back to 1997. typos and all. got ideas?
Back in 1997, I registered my first domain benforpresident.org. It was a silly site that I would do almost nothing with. I had grand plans for a genuine run for 2016. With technology on my side, how could I fail? Well, I missed a registration payment and it was snatched from me. Oddly, the content remained the same in the hands of it’s new owner. Nothing was added, nothing was changed. (apart from some tracking javascript). Yesterday on a whim, I checked it’s availability and reacquired it. I don’t know exactly what I am going to do with it, but for now, I have set the clock back to 1997. typos and all. got ideas?
Apple’s goto fail bug and what it means to you?
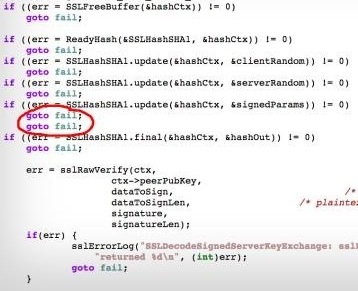 The security community went into a frenzy this weekend over Apple’s latest iOS security update. On Friday, Apple quietly released iOS 7.0.6 and 6.1.6 to patch a bug in its SSL implementation. This particular bug nicknamed “goto fail” for the actual contents of its source code behind the error. Basically, one too many goto fail causes the fail not to be conditional, but absolute. This failure allows Apple’s SSL framework (the technology that secures web transmissions) to be easily bypassed. In other words, Safari, Mail, Calendar, Software Update, as well as any 3rd party applications who take advantage of Apple’s SSL libraries could potentially have their communications intercepted by an unscrupulous individual. Apple claims that it is a type-o, but many wonder if this might be a deliberate backdoor (one that has lasted over a year).
The security community went into a frenzy this weekend over Apple’s latest iOS security update. On Friday, Apple quietly released iOS 7.0.6 and 6.1.6 to patch a bug in its SSL implementation. This particular bug nicknamed “goto fail” for the actual contents of its source code behind the error. Basically, one too many goto fail causes the fail not to be conditional, but absolute. This failure allows Apple’s SSL framework (the technology that secures web transmissions) to be easily bypassed. In other words, Safari, Mail, Calendar, Software Update, as well as any 3rd party applications who take advantage of Apple’s SSL libraries could potentially have their communications intercepted by an unscrupulous individual. Apple claims that it is a type-o, but many wonder if this might be a deliberate backdoor (one that has lasted over a year).
The real tragedy of this issue is that it effects Mavericks (Mac OS 10.9.x) as well as iOS, but there is yet no official fix for Apple Computers. Update Published by Apple! Apple desktops, laptops, and iMacs are now were left in a very dangerous position: unprotected to a known threat. I am sure that the bad guys are already configuring their sslstrip, sslsniff, or similar tools. Accounts will be compromised, communications will be intercepted or manipulated, or in the case of software updates, malware could even be introduced.
What can we do? First off, run the 7.0.6 update on any iOS devices not yet up to date. Do this from a trusted wifi, not a public one. With your mac, avoid public wifi until this is resolved. Avoid Apple Mail except when absolutely necessary and only from trusted networks. Only use Google Chrome for secure web browsing (it uses its own SSL framework). Optional: Install @i0n1c’s binary patch. @i0n1c’s patch fixes the bug, but may break other things. Run Apple 10.9.2 update!
links:
Test your system: https://gotofail.com/
Great Writeup: https://www.imperialviolet.org/2014/02/22/applebug.html
Quick & Dirty Patch: http://www.sektioneins.de/en/blog/14-02-22-Apple-SSL-BUG.html
Official Apple Fix http://support.apple.com/kb/HT6150
ISP Migration Underway!
 You will have to excuse the recent lack of posts. I have been in the process of packing up and moving all my domains to their new host, Site5. This has been a particularly arguious journey, as I have been with my old host for nearly a decade. Many of my sites were custom, undocumented and needed to be moved by hand. This post is itself a test of my syndication.
You will have to excuse the recent lack of posts. I have been in the process of packing up and moving all my domains to their new host, Site5. This has been a particularly arguious journey, as I have been with my old host for nearly a decade. Many of my sites were custom, undocumented and needed to be moved by hand. This post is itself a test of my syndication.
Linked In added to the growing list of leaked passwords!
Change your password immediately as well as any other accounts with the same or similar passwords. Another lesson in password reuse will undoubtably trickle down over the next few days and weeks. At least the passwords weren’t stored in the clear, though I don’t think they were salted. when will we learn?